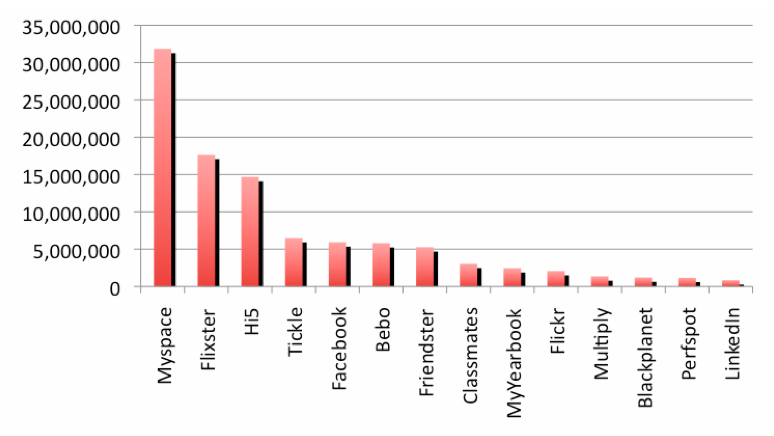
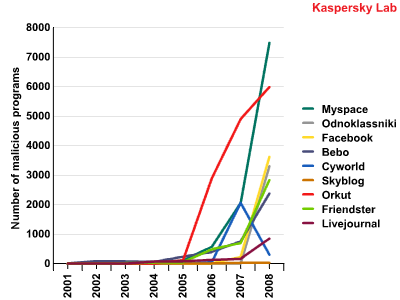
Social networking websites are not only to communicate or interact with other people globally, but also one effective way for business promotion. Relevance of the study due to the fact that with increased number of users of social networks, the number of attacks carried out by hackers to steal personal information and use of your user account in order to send unauthorized messages called spam is also raised. To address these security issues, network and security managers often turn to network policy management services such as firewall, Intrusion Prevention System (IPS), antivirus, and Data Loss Prevention systems (DLP).
Online Social Networks (OSN) such as Facebook, Tweeter, MySpace etc. play an important role in our society, which is heavily influenced by the Information Technology (IT). In spite of their user friendly and free of cost services, many people still remain reluctant to use such networking sites because of privacy concerns. Many people claim, these sites have made the world more public and less private – consequently a world with less morale is evolving. Some consider this social change as positive because people are more connected to each other. Nowadays, millions of internet users regularly visit thousands of social website to keep linking with their friends, share their thoughts, photos, videos and discuss even about their daily-life. Social networks can be traced back to the first email which was sent in 1971 where two computers were sitting right next to each other. In 1987 Bulletin Board System exchanged data over phone lines with other users and lately in the same year the first copies of early web browsers were distributed through Usenet. Geocities was the first social website founded in 1994. Theglobe.com launched in 1995 and gave people the ability of interacting with others, personalize and publish their files on the Internet. In 1997, the America on Line (AOL) Instant Messenger was lunched. In 2002, Friendster was lunched and within three months more than 3 million users were using it. In 2003, MySpace was lunched and in the following years many other social networking sites were lunched such as Face book in 2004, Twitter in 2006 etc [1].
There are so many social networking sites and social media sites that there is even search engine for them [2]. Further, there are specialized websites which allow users to create their social networking sites such as Ning and KickAppls [3]. These social websites have had positive and negative impacts; so many people waste most of their time on using these websites, which results in losing their jobs or colleges or even their natural social lives and families! Many others post copyrighted materials without authorizations, or pornographic or illegal contents. Some of the users, smart-users, use social networking websites in a very positive way; as happen now in the Spring of Arab World!
The Internet today, unfortunately, offers to the cybercriminals many chances to hack accounts on social network sites and the number of malicious programs that target the social web sites is very huge. (Ref: Figure 2)
The rest of the paper is organized as follows. Section 2 discusses the security policy background. In Section 3, we present the categorized types of social networks. In Section 4, we discuss and analysis the cyber threats in social websites. In Section 5, it has been recommended the anti-threats strategies. In Section 6, the future trends of social networks have been analyzed. In Section 7, we reveal the risks prevention and threats vulnerabilities. Finally, we ended our paper with the conclusion at Section 8.
SECURITY POLICY BACKGROUND
In spite of an organization’s size, their businesses, or the extent to which it uses technology, information security is an important matter that should be addressed by explicit policies. However, the settlement of security policies is itself based on a specific framework that requires methodology to write, structure, effective review, approval, enforcement and awareness process [6]. Although this paper doesn’t have the goal to stress the topic security policies, the most important factor to be
considered to develop the proposed framework is having an established security policy. Security policies are high-level statements that provide guidance to those who must make present and future decisions. An information security policy document is vital for many reasons. Beyond the definition of roles and responsibilities for workers, partners, suppliers, a policy document sensitizes them to the potential threats, vulnerabilities and problems associated with modern information systems. A consistent awareness program is fundamental to achieve the security policy goals. Education and training helps minimize the cost of security incidents, and helps assure the consistent implementation of controls across an organization’s information systems. Currently the effectiveness of security policies considering data leakage is an important concern. Regardless of the type or mode of data leakage, recent research [9] reveals that one out of four companies does not even have a security policy and for businesses with policies, the findings reveal a significant gap between the beliefs of security staff regarding employee compliance and the actual behavior of them. The reasons why employees knowingly overlook or bypass security policies and put corporate data at risk are mainly a result of a failure to communicate the security policies and create an awareness behavior. The proposed framework presents an adaptive strategy to the awareness program. A security policy detailing information classification is essential to sustain a framework to avoid data leakage. This policy will create the basis of ownership responsibilities for files, databases and other shared information, indicating who have been granted authority to originate, classify, modify, or delete specific information. The policy should also indicate the transportation mode, third-party interactions, labelling, life cycle, declassification, and information destruction. Depending on the information type and its criticality to the owner, the information may be assigned, for example as public, secret, confidential or internal use only.
TAXONOMY OF SOCIAL NETWORKS
Generally, a social network is a social structure made up of individuals or organizations, which are connected, by one or more specific types of interdependency, such as friendship, common interest, and exchange of finance, relationships of beliefs, knowledge or prestige. Social networks can also be defined as those websites that enable people to form online communications and exchange all types of data. It includes the following.
First, Social networking sites such as MySpace, Face book, Windows Live Spaces, Habbo, etc. and the second Social media sites such as You tube, Flicker, Digg ,Metacafe, etc. Table 1 illustrates the social websites according to continent and regions.
Table 1. Social websites according to Continent and Region
| Continent/region | Dominant social websites |
| Africa | Hi5, Facebook |
| America (North) | MySpace, Facebook, Youtube, Flicker, Netlog |
| America (Central &South) | Orkut, Hi5, Facebook |
| Asia | Friendster, Orkut, Xianonei, Xing, Hi5, Youtube, Mixi |
| Europe | Badoo, Bedo, Hi5, Facebook, Xing, Skyrock, Ployaheod,Odnoklassniki.ru.V Kontakte |
| Middle East | |
| Pacific Island | Bedo |
In table 2, the top five popularity trafficked social media sites:
Table 2. Top five popularity trafficked social media sites
| Site Name | Primary Shared Media |
| YouTube | Videos |
| Flicker | Images |
| Digg | Book marks |
| Metacafe | Videos |
| Stumbleupon | Cool Contents |
Moreover, Youtube is the third most visited Web Site after Yahoo and Google but flicker is the 39th most visited web site [5].
CYBER THREATS IN SOCIAL NETWORKING WEBSITES
Lately, social networks attract thousands of users who represent potential victims to attackers from the following types (Ref: Figure 4) [6, 7]. Phishing is a form of social engineering in which an attacker attempts to fraudulently acquire sensitive information from a victim by impersonating a trustworthy third party. Phishing attacks today typically employ generalized “lures”. For instance, a hacker misrepresenting himself as a large banking corporation or popular on-line auction site will have a reasonable yield, despite knowing little to nothing about the recipient. Phishing attacks can incorporate greater elements of context to become more effective. In other forms of context aware phishing, an attacker would gain the trust of victims by obtaining information about their bidding history or shopping preferences. Phishing attacks can be honed by means of publicly available personal information from social networks [9]. First hackers and spammers who use social networks for sending fraudulent messages to victims “friend”, Cybercriminals and fraudsters who use the social networks for capturing users data then carrying out their social-engineering attacks and Terrorist groups and sexual predators who create online communities for spreading their thoughts, propaganda, views and conducting recruitment.
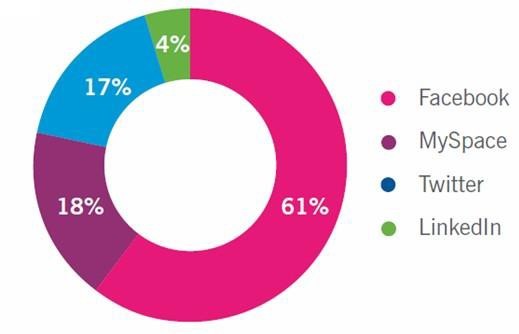
Figure 3. Threats percentage-pose on social networks (Sophos 2010 Security Threat Report) Cyber threats that might the users face can be categorized into two categories.
Privacy Related Threats
Privacy concerns demand that user profiles never publish and distribute information over the web. Variety of information on personal home pages may contain very sensitive data such as birth dates
home addresses, and personal mobile numbers and so on. This information can be used by hackers who use social engineering techniques to get benefits of such sensitive information and steal money.
Traditional Networks Threats
Generally, there are two types of security issues: One is the security of people. Another is the security of the computers people use and data they store in their systems. Since social networks have enormous numbers of users and store enormous amount of data, they are natural targets spammers, phishing and malicious attacks. Moreover, online social attacks include identity theft, defamation, stalking, injures to personal dignity and cyber bulling. Hackers create false profiles and mimic personalities or brands, or to slander a known individual within a network of friends.
ANTI THREATS STRATEGIES
Recent work in programming language techniques demonstrates that it is possible to build online services that guarantee conformance with strict privacy policies. On the other hand, since service providers need private data to generate revenue, they have a motivation to do the opposite. Therefore, the research question to be addressed is to what extent a user can ensure his/her privacy while benefiting from existing online services. A novel approach, called NOYB (None Of Your Business), was discussed in [7], which provides privacy while preserving functionalities provided by service providers. Users willingly share personal identifying information, but do not have a clear idea of who accesses their private information or what portion of it really needs to be accessed. OSNs can be examined from a viewpoint of characterizing potential privacy leakage [10]. That is, we can identify what bits of information are currently being shared, how widely they are available, and what users can do to prevent such sharing. The third-party sites that track OSN users play a major role in these kinds of attacks causing privacy leakage on popular traditional websites. In the long run, we can identify the narrow set of private information that users really need to share to accomplish specific interactions on OSNs so that privacy can be enhanced further. Privacy can also be preserved by restricting the ability to recover the real data from the fake data to authorized users only.
In this section we present the different types of cyber threats in social networks and found the most of threats happens due to the factors which are listed as below:
- Most of the users are not concern with the importance of the personal information disclosure and thus they are under the risk of over disclosure and privacy invasions,
- Users, who are aware of the threats, unfortunately choose inappropriate privacy setting and manage privacy preference properly,
- The policy and legislation are not equipped enough to deal with all types of social networks threats which are increase day by day with more challenges, modern and sophisticated technologies,
- Lack of tools and appropriate authentication mechanism to handle and deal with different security and privacy issues,
Because of the above mentioned factors that cause threats, we recommended the following strategies for circumventing threats associated with social website:
- Building awareness the information disclosure: users most take care and very conscious regarding the revealing of their personal information in profiles in social websites,
- Encouraging awareness -raising and educational campaigns: governments have to provide and offer educational classes about awareness -raising and security issues,
- Modifying the existing legislation: existing legislation needs to be modified related to the new technology and new frauds and attacks,
- Empowering the authentication: access control and authentication must be very strong so that cybercrimes done by hackers, spammers and other cybercriminals could be reduced as much as possible,
- Using the most powerful antivirus tools: users must use the most powerful antivirus tools with regular updates and must keep the appropriate default setting, so that the antivirus tools could work more effectively,
- Providing suitable security tools: here, we give recommendation to the security software providers and is that: they have to offers some special tools for users that enable them to remove their accounts and to manage and control the different privacy and security
FUTURE TRENDS OF SOCIAL NETWORKING WEBSITES
In spite of the development and advanced technologies in social networking websites adjustment, a few are listed as below:
- A need for more improvements for social networks so that they can allow users to manage their profiles and connecting tools,
- A need for convergence and integration of social networks and future virtual worlds,
- Needs for data integration from different networks, e. identification of all contents related to specific topic. This needs particular standards and sophisticated technology supported by social networks providers,
- Many social networks need standard application programming interfaces, so that users can import and export their profiling information by using standard (For example, Facebook and Google have applied new technologies that allow user data portability among social websites, representing a new source of competition among social networking service),
We hope that in the near future, one can by single sign-in functionality use over websites, that is, the user IDs are portable to other websites.
Moreover, virtual worlds have distinct virtual economies and currency that based on the exchange of virtual goods. Games are one of the newest and most popular online application types on social websites. Here, we have to mention the importance of privacy and security to save users from fraudsters who attempt to steal social networking credentials and online money.
Finally, we have to mention that the advances in the social websites and mobile-phone usage will effect on the growing of using mobile social networking by adding more features and application not only to mobiles, but also to social televisions for future chat, email, forums, and video conferencing [8, 9].
RISKS PREVENTION AND THREATS VULNERABILITIES
In this Section, we supply with some important recommendations to help social network users stay save by applying the followings:
- Always have very strong passwords on your emails and other social web sites,
- Limiting the provided personal information in the social web sites as much as you can,
- Change your passwords regularly, so that your information can be out of reach by hackers,
- Provide with the minimum amount of information to the website and internet due to the publicity of the internet,
- Don’t trust online others and don’t answer on special questions from unknown users or companies e. be skeptical,
- Check privacy policies and be aware of unknown emails and links provides by unknown users,
- To prevent detecting emails address by spammer techniques, write the email: xyz@hotmail.com as xyz at hotmail dot com.
SUMMARY
Although social networking websites offer advanced technology of interaction and communication, they also raise new challenges regarding privacy and security issues. In this paper, we briefly described the social networking web sites, summarized their taxonomy, and highlighted the crucial privacy and security issues giving some essential anti-threats strategies with the perspective of the future of the social networking websites.
We think that the advancement of new technology in general and social websites in particular will bring new security risks that may present opportunities for malicious actors, key loggers, Trojan horses, phishing, spies, viruses and attackers. Information security professionals, government officials and other intelligence agencies must develop new tools that prevent and adapt to the future potential risks and threats. It can also safely manipulate the huge amount of information in the internet and in the social websites as well.
[1] http://www.onlineschools.org/blog/history-of-social-networking/
[2] Social networking sites search engine, http://findasocialnetwork.com/search.php.
[3] B. Stone, Is Facebook growing up too fast, The New York Times, March 29, 2009 [4] “Using Facebook to Social Engineer Your Way Around Security”,
http://www.eweek.com/c/a/Security/Social-Engineering-Your-Way-Around-Security-With-Facebook-277803/ 05.20.2010
[5] www.securelist.com, «”Instant” threats», Denis Maslennikov, Boris Yampolskiy, 27.05.2008.
[6] Won Kim , Ok-Ran Jeong, Sang-Won Lee , “On Social Websites” , Information Systems 35 (2010), 215-236.
[7] Kaven William, Andrew Boyd, Scott Densten, Ron Chin, Diana Diamond, Chris Morgenthaler, ” Social Networking Privacy Behaviors and Risks” ,Seidenberg School of CSIS, Pace University, White Plains, NY 10606, USA.
[8] Abdullah Al Hasib, “Threats of Online Social Networks”, IJCSNS, Vol. 9, No 11, November 2009.
[9] Anchises M. G. de Paula, “Security Aspects and Future Trends of Social Networks”, IJoFCS (2010) , 1, 60-79.
[10] D. Boyd, N. Ellison, Social network sites: definition, history, and scholarship, Journal of Computer- Mediated Communication 13 (1) (2007) article 11.
[11] Gilberto Tadayoshi Hashimoto, Pedro Frosi Rosa, Edmo Lopes Filho, Jayme Tadeu Machado, A Security Framework to Protect Against Social Networks Services Threats, 2010 Fifth International Conference on Systems and Networks Communications.
[12] “Data Loss Prevention Best Practices”, http://www.ironport.com/pdf/ironport_dlp_booklet.pdf 05.20.2010.
[13] “The Real Face of KOOBFACE: The Largest Web 2.0 Botnet Explained”, http://us.trendmicro.com/imperia/md/content/us/trendwatch/researchandanalysis/the_real_face_of_koobface_jul2009.pdf 05.19.2010.