If you are using wireless infrastructure in your network, you should monitor all access points for any breaches and changing all security codes are essential.
3. Scan for affected machines,
Make sure you check every machine that could potentially be hacked for compromises. Also check whether root kits and other hacking tools are installed on the computer.
4. Disable suspicious user accounts,
If there is any suspicious user accounts that you think it might be a victim, disable it.
5. Change passwords,
This especially includes the Administrator account and accounts that are used to start services on the server. Consider complexity in your password policy.
6. Preserve the data,
If possible, buy replacement hard drives for the hacked computers, so that you can preserve the hacking activity on the compromised computer. After you’ve restored the network, you can review this information to gain more valuable information about the hack.
7. Identify and address the vulnerability,
Run a vulnerability assessment test to identify week points.
8. Rebuild the machine,
After a machine has been hacked, it’s almost impossible to completely clean it of all hacking tools. The only way to make sure the machine is clean is to format the hard drives and rebuild the computer from scratch.
9. Bring the network back up,
Make sure you’ve closed all holes on your network, to prevent the hacker from returning and carefully monitor the network.
10. Perform forensic analysis on the hard drives,
Document each hacking tool that you find on a computer. These are useful information, which you need them in your vulnerability assessment or in your penetration test practices.
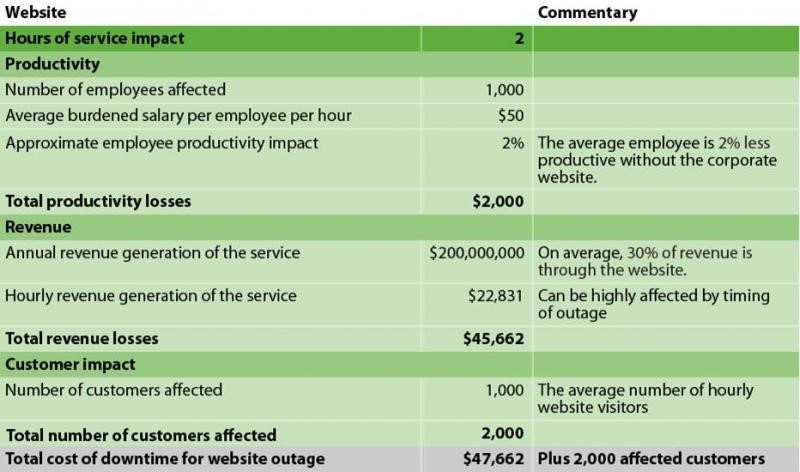
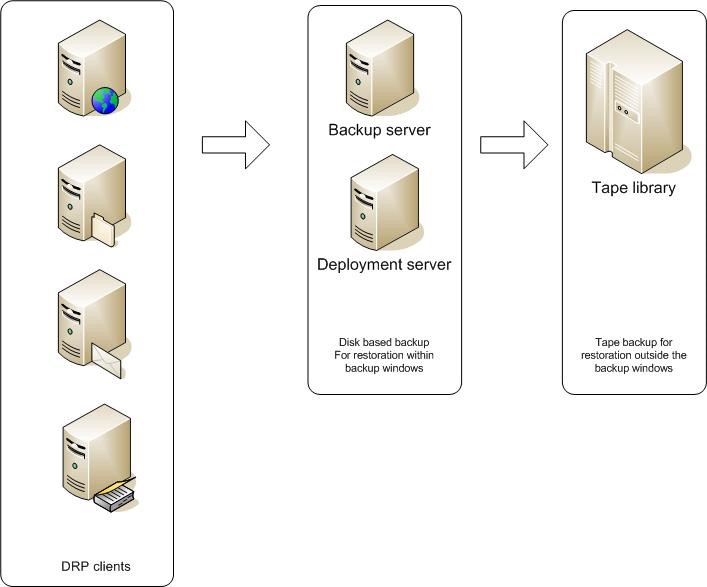
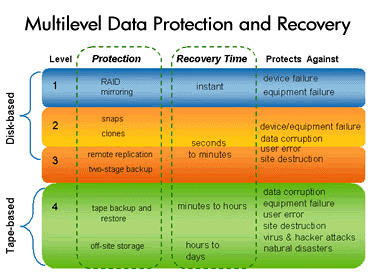
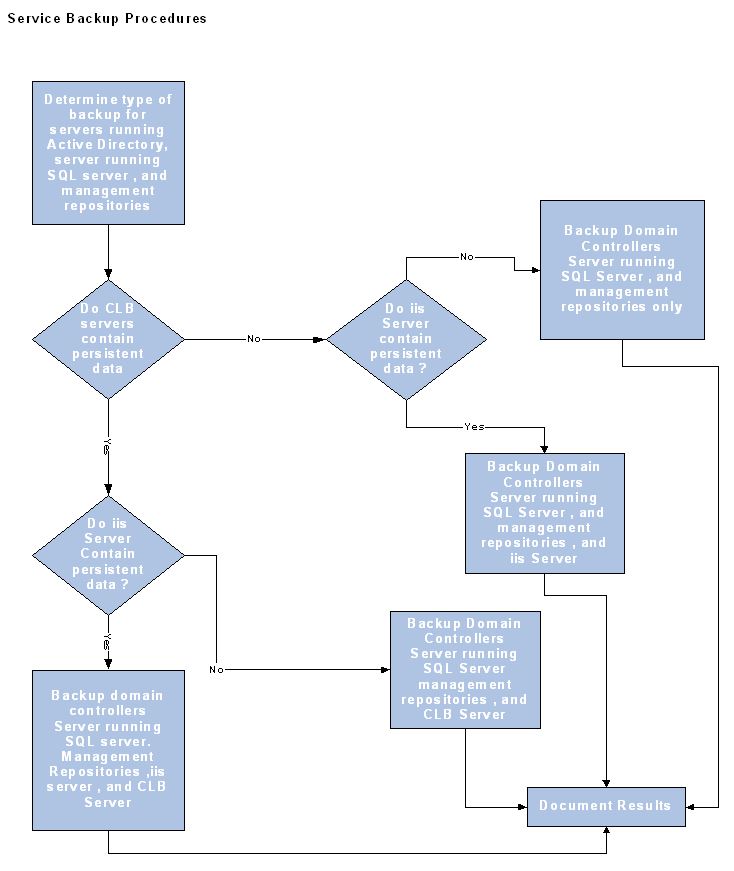
Summary
As you can see, the disaster recovery plan should be a conjunction of business continuity plan. Both are just a part of the complete business continuity/disaster recovery plan and if one is missing, the plan will not work properly. While business continuity is very important, but since in disaster recovery phase, we are still facing the phenomenon, we can say disaster recovery is the vital part. Therefore we need to make sure that our disaster recovery plan is healthy and ready to work for us by keeping them up-to-date. Checking the disaster recovery time to time is advised which