We are living in a world, which our life is twisted with technology. Technology helps us to shine our life and make it easier and more fascinating. We use it when we want to talk to our beloved ones over the distance, or when we want to make a job done in the minimum possible time or when we want to control our financial accounts. For sure we need to secure not some but all of them. When it comes to the securing and protecting, the level of security matters in each category, and the first step in all categories is “Authentication”. We need to be authenticated to protect our valuable moments or assets, and to perform this task, “Passwords” are to help us. In this article we are going to open a new window to the concept of passwords and practically explain why we need to develop Password concept.
It happens!
As Scott Pinzon1,2 also says, when an attacker goes to use the password he has captured, first of all he must decrypt it.
To decrypt passwords, usually attackers choose from many different tools, which are known as password crackers. Some are expensive commercial programs and some are free for everyone to download from the Internet and use. And good or bad, people do by the thousands.
If you are an attacker, typically you would snick on to the network, locating the password file and then send a copy of it to yourself, so you can crack it at your convenience or you can capture encrypted passwords traveling across the network as users trying to login.
Rainbow Tables and Brute Force Attack
Once you have encrypted passwords, probably you will start to lunch the whole arsenal of automated attacks to decrypt them. For example you might perform the dictionary attack in many languages. You might also perform a dictionary hybrid attack. Computer users who know about the dictionary attacks would garble the passwords so it is not a dictionary word. For example if a password contains “world” you might spell it “w0r1d”. You can also resort to brute force.
Brute force means calculating every possible password and trying each one. This considers the last resort because performing all those calculations is slower. But slow is a relative term!
To encrypt a password Windows performs a mathematic formula on it called “hash”. A hash is a number generated from a string of text. It is easy to go from the text to the hash, but should be impossible to look at the hash and figure out the text. That is the reason they call it also “a one-way hash”. But the Windows hash formula is widely known. So password cracker can take a list of words, hash each one and see of the result if matches any of the hashed words in the encrypted file. Even an old Pentium II PC can calculate and compare hashes on a rate of almost a million tries per second. A Pentium IV machine can check almost five million per second. So if outdated PC can calculate and try millions of possible password per second why do we say brute force is slow?
Because a password with only ten characters in ASCII, has more than 1 thousand trillion possible character combinations. To be precise there are 1,180,591,620,717,411,303,424 different possible combinations.
Even going thorough combinations at a rate of 5 million per second it would take around seven and a half million years for a Pentium IV computer to try all possible combinations and for each character you add to the length of the password, the number of possible combination increases exponentially. But we are not using old computers with old technologies anymore and moreover, new techniques are born day to day.
There are people, who have calculated all the possible hashes for all the passwords, and they would save the result for the others to use. We refer to this as a rainbow table.
What is Rainbow Table?
Rainbow tables are a tool used to reverse one-way cryptographic hashes such as MD5, NTLM and SHA1. Using complex mathematical formulas, it can cover large password key spaces in a short time
Rainbow tables are a middle ground between brute force and dictionary attack. Rainbow tables cover most of the key-space (usually > 99.9% of the key-space) and do it in a time that is much faster than brute force attacks. The key to doing this is by using pre-computed files, rainbow tables, with complex mathematical formulas to reverse the cryptographic hashes. The reasoning behind rainbow tables is most of the work is done once upfront, so you don’t have to do very much work when you need to reverse a hash.
By using a rainbow table computers get to perform matches instead of calculations. This goes much faster and that’s is why we say brute force is slow. But brute force is guaranteed effective if the attacker has enough time.
In this article we are not going to elaborate rainbow tables, but we are going to see how we can bundle some good free tools to crack password by brute force and button line, why a good password is important. For sure a good rainbow table is the fastest way to crack a hashed password, but sometimes we know some characters of the password and if we use brute force technique we can be faster. And rainbow tables occupy lots of spaces and keeping them is a problem which not every ordinary user can accommodate them. Besides for those routers use WiFi Protected Setup (WPS), brute force could be a good option.
A typical Scenario
Lets presume that we want to hack our wireless router. Our wireless router is configured to use WPA2 Pre-shared Key. We suppose that we got the WPA handshake and we already have it. It is done easily with lots of handy tools. Now we want to use brute force attack to crack the hashed password.
As we understood from the above, brute force is a slow solution, but how can we make it faster?
By the power of cloud computing, we can make brute force faster. For example a WPA2 password of a WPS-enabled wireless router, which contains only numbers, can be cracked by a pool of GPUs very fast.
There are lots of cloud-computing services nowadays and one of my favorites is Amazon Elastic Compute Cloud (Amazon EC2). It has various options even per hour for as low as 2 US Dollar3!
Why do we insist on GPU while we can go directly for GPU? There are lots of reasons but the main reason, which is important to us, is that a GPU can handle lots of repetitive parallel processes in a better and faster way, which makes it ideal for our need. More comparisons per second, faster the result comes up.
What are the good ones?
One of the good tools among password crackers is the John the Ripper4 (Figure 1). John can generates passwords for us (which this is just one of its functionality) and we can use them in Pyrit5 (Figure 2) which is a massive hash database creator and then use the results in coWPAtty6 (Figure 3) to crack the password.
We can also use Crunch7 to make the wordlist and Aircrack-ng8 to crack the password but I leave them on you to try them on your spare playing time! All these tools are open source and free to use.
We just assume you know the tools and have them installed on you machine. We just focus on important parts and explain those necessary switches as this is not a training article but just an awareness of how passwords are important.
Roadmap to our goal:
This is our roadmap: With John we are going to generate possible combinations and export them to Pyrit to pre-compute the Pairwise Master Keys (PMK) with the power of GPU and then with coWPAtty to compare and crack the WPA2 handshake and reach to the password.
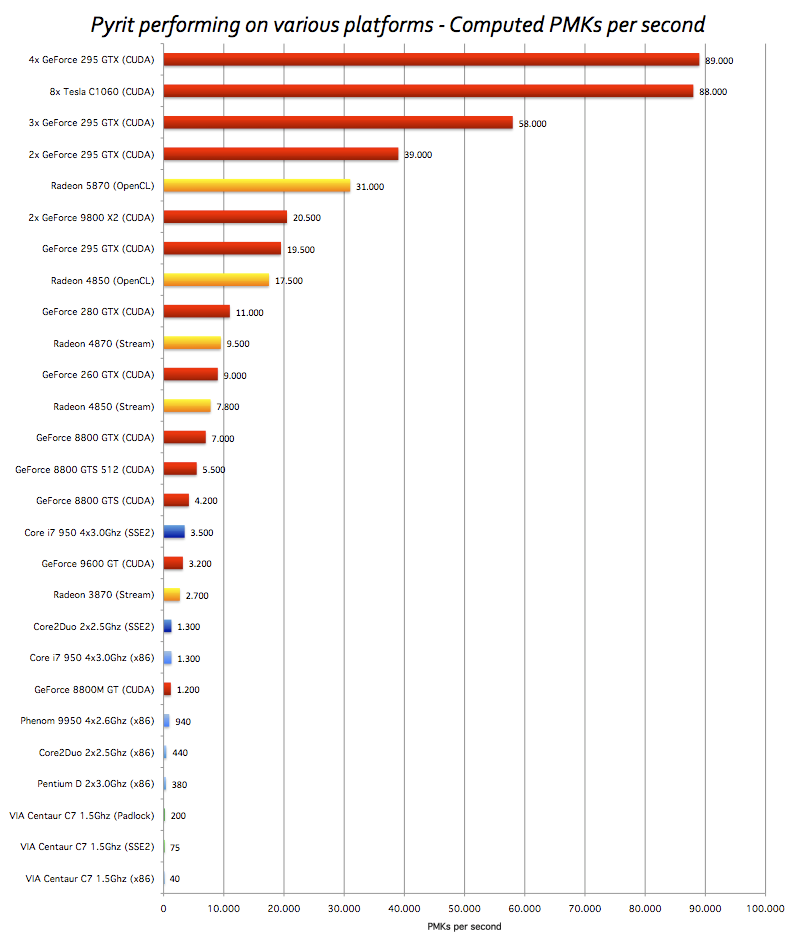
Pyrit is rapid and the rate of its speed is totally up to the speed of your GPU and how many cores you want to utilize (Figure 4). Consider that Pyrit is not the best and if you really want to make the procedure quick maybe better to go for Hashcat9 which computes millions PMKs per second.
If you want to check if Pyrit has recognized your computational cores you can use ./pyrit list_cores and for checking the performace of Pyrit on your current hardware configuration, you can use ./pyrit benchmark which runs a test on the available cores on your machine.
Taking the action
So we start with John, to generate the passwords list:
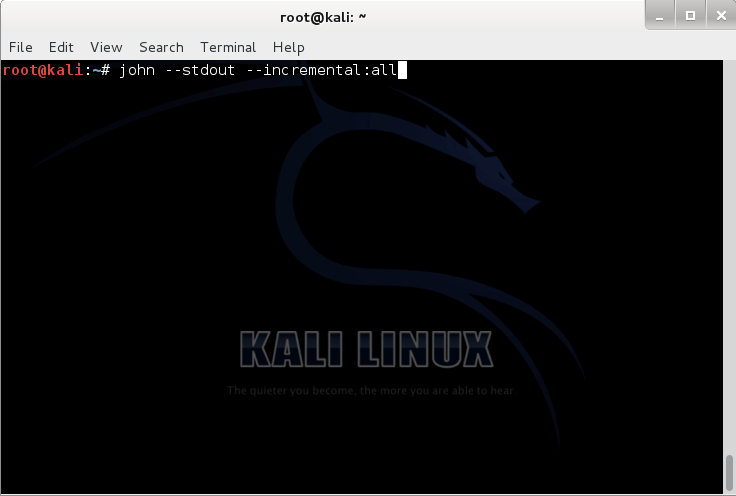
./john –-stdout –-incremental:all
As we are just going to lease a pool of GPUs and usually these services are dedicated and we cannot find much space there, we don’t need John to store generated passwords. So what we exactly need is that John generates them and just echo them out. Here we use –-stdout switch. With –-incremental:all we tell John to generate passwords with all possibilities (Figure 5).
–-incremental switch has different modes as: all, alnum , alpha, digits and lanman which you can choose among based on your requirement. The mode we chose is suitable for the full printable US-ASCII character set and to try all possible password lengths from 0 to 8. If you need to check for more characters in length, you can go for Crunch.
Obviously we need to pipe this command with the next one, which is Pyrit to compute the hashes. Here is the command:
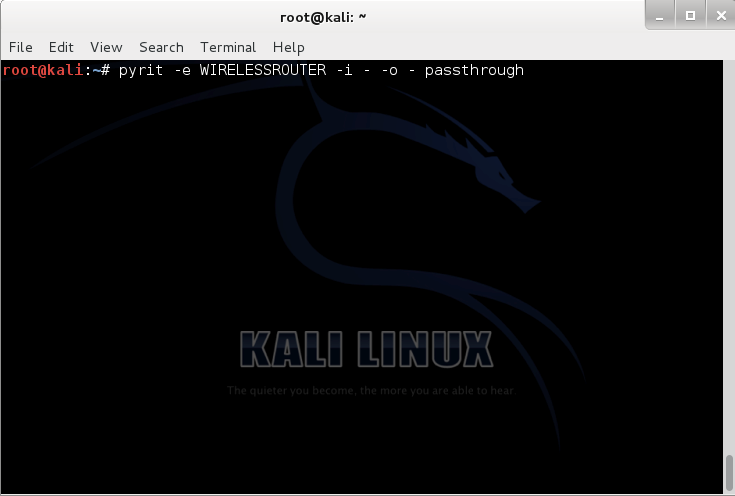
./pyrit –e WIRELESSROUTER –i – -o – passthrough
With switch –e WIRELESSROUTER we tell Pyrit what is the ESSID where “WIRELESSROUTER” should be replaced with the correct name of the accesspoint. With –i – we tell Pyrit that there is no input file as wordlist and it should just use whatever it gets from –-stdout of John as –-stdin. With -o – and Passthrough Pyrit understands that it should send out the results as –-stdout to the next piped application, which is coWPAtty. We use this output format when we have problem with storage and we don’t want to make a database in coWPAtty binary format (Figure 6).
And the last step is to crack the file with coWPAtty. The command is as follow:
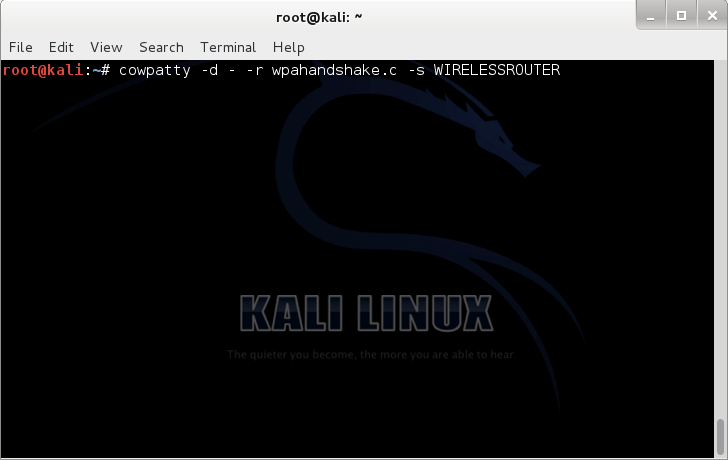
./cowpatty -d – -r wpahandshake.cap -s WIRELESSROUTER
With a quick look at this command we can understand that with -r wpahandshake.cap we are defining the captured WPA handshake, which is going to be cracked, and with -s WIRELESSROUTER we define the ESSID and the -d – switch defines the output which simply says nothing but our screen (Figure 7)!
So here it is a quick way to generate passwords, make their hashes and crack the captured handshake.
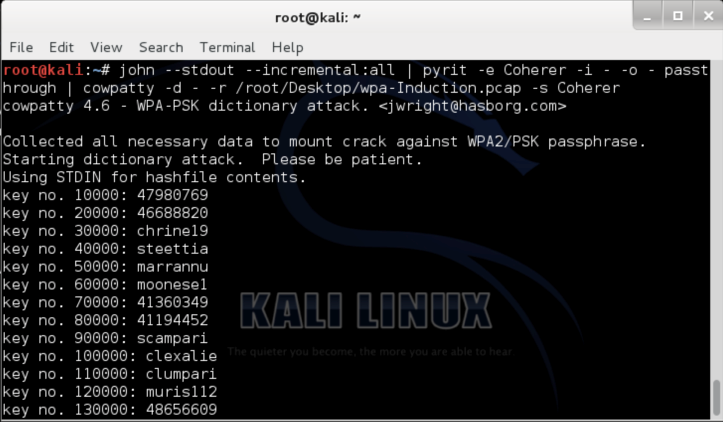
So the full command we may use is as follow:
john –-stdout –-incremental:all | pyrit –e WIRELESSROUTER –i – -o – passthrough | cowpatty -d – -r wpahandshake.cap -s WIRELESSROUTER
Here we are going to crack the password and good or bad news is if we use a strong platform and enhanced tools like Hashcat we can do it very fast, and if your password is weak, you are welcome to the intruder.
Bottom line
The speed of cracking passwords are getting faster and faster and all those security mechanisms and protocols, which were relying on the long duration of the cracking procedure, are getting closer to their apocalypse.
For now, as there is no other options among the protocols and security mechanisms, we need to defend and one of the ways is to make the length of the password which we use, longer.
Obviously longer passwords are stronger. But how long is long enough? How many characters does a password need in order to realistically slow down an attacker.
We recommend you use 15 characters or more in your password. And one of the ways to defend is to think that the age of passwords is over and instead of thinking “Pass-word” it is better to think, “Pass-phrase”.
But how do you think got a long crack resistant password
No password is totally unbreakable. But if it takes for an attacker more than a week to crack your password, although he gives up and move to an easier target.
So now we really need to think how strong, not passwords, but passphrases matter.
1 http://www.youtube.com/watch?v=6bNtMPKafk0
2 http://www.scottpinzon.com
3 http://aws.amazon.com/ec2/pricing
4 http://www.openwall.com/john/
5 https://code.google.com/p/pyrit/
6 http://wirelessdefence.org/Contents/coWPAttyMain.htm
7 http://sourceforge.net/projects/crunch-wordlist/
8 http://www.aircrack-ng.org
9 http://hashcat.net/oclhashcat-plus/